Austin IT Support Provider Shares How to Close Hidden Cybersecurity Gaps
Most companies assume their insurance policies will protect them from cyber threats until reality proves otherwise. A single breach can cripple revenue, erode customer trust, and tarnish a brand in just a few hours.
The 2025 IBM Cost of a Data Incident Report estimates the average cost of a cyberattack at $4.44 million. That’s a financial crisis.
| Kent Morris, President of Gravity Systems, says, “Cyber resilience begins long before an attack. It’s about preparing, measuring, and owning the risks you can control.” |
This is where a cyber insurance coverage checklist becomes indispensable.
It helps you:
- Distinguish between meaningful coverage and vague policy language
- Identify gaps in protection before they become liabilities
- Align insurance terms with your actual risk exposure and business operations
In this article, an Austin IT support provider explains why gaining clarity is critical in a world of rising threats and shifting policies — and how a well-crafted checklist turns uncertainty into confidence, transforming your insurance from a safety net into a strategic asset.
Preparing a Cyber Insurance Coverage Checklist: Start with Your Risk Reality
You can’t build the right safety net without understanding where you’re standing. Every business faces unique digital threats, and insurers assess your cyber risk profile to determine coverage terms, pricing, and exclusions.
Begin by evaluating your company’s exposure across three key dimensions:
- Data Sensitivity: The more personal, financial, or regulated data you store, the higher your exposure. If your systems handle payment information or protected health records, your checklist should prioritize coverage for forensic investigation, legal defense, and breach notification costs.
- Remote Access: Every remote login is a potential entry point. Businesses with hybrid or remote teams face stricter policy requirements and higher premiums due to increased attack surfaces.
- Vendor Dependencies: Your risk doesn’t stop at your firewall. If a third-party provider, like a payment processor or SaaS vendor, is breached, your business could suffer collateral damage. Coverage should account for shared liability and downstream impact.
Quick Reference Guide
| Risk Level | Traits |
| Low-Risk Profile | Limited data collection, few third-party vendors, internal systems only |
| High-Risk Profile | Cloud-heavy operations, remote workforce, sensitive customer data, frequent vendor integrations |
Understanding your risk profile helps you tailor your cyber insurance coverage checklist, deciding what risks to absorb and which to transfer. It’s the first step toward building a policy that protects your business where it matters most.
The Core of Every Strong Cyber Insurance Coverage Checklist
A solid cyber insurance policy is built on real-world protection strategies. When a breach happens, what matters most is what your policy actually covers. That’s why your cyber insurance coverage checklist should include these non-negotiable elements:
- Forensic and Investigation Costs: You’ll need cybersecurity experts to determine what happened, how it happened, and what remains vulnerable. Without this, recovery slows and losses escalate.
- Legal and Regulatory Defense: If personal or customer data is compromised, lawsuits and regulatory scrutiny are inevitable. This coverage shields you from fines, legal fees, and compliance penalties.
- Notification and PR Costs: Many jurisdictions require prompt disclosure to affected parties. Coverage here pays for breach notifications, which could cost up to $5,000, as well as crisis communications, and media management to protect your reputation.
- Business Interruption and Ransom Payouts: Ransomware can freeze operations. The right policy offsets lost income, ransom demands, and downtime, keeping your business afloat during chaos.
- Data Restoration and Third-Party Loss Coverage: Recovering data can be costly. This protection covers restoration expenses and compensates partners or customers if they suffer damages due to your breach. Some breaches require you to reload all systems (desktops, laptops, servers), and take a lot of manpower to recover from.
Each of these components ties directly to business continuity. Without them, you’re gambling with your operations and reputation. Insurers also assess how well your coverage aligns with cyber insurance policy requirements when pricing renewals, so a complete checklist is not a one-off protection; it pays off in the long term.
How to Match Your Coverage with Your Business Size
A mere 17% of small businesses maintain cyber insurance, compared with 84% of bigger organizations. Not every company needs a million-dollar cyber insurance policy, but every business needs the right one.
The key is to scale coverage based on your operational footprint, risk exposure, and regulatory obligations. Here’s how to align your coverage with your size:
- Small Businesses
Focus on essentials like:- Data restoration
- Forensic investigation
- Ransomware response
You may not face regulatory lawsuits, but even short-term downtime can be financially devastating.
- Mid-Sized Firms
Expand coverage to include:- Third-party loss protection
- Business interruption insurance
Hybrid IT setups and partial cloud adoption increase dependency risks, making broader coverage critical.
- Enterprises
Prioritize comprehensive protection:- Multi-region coverage
- Regulatory response costs
- Vendor liability and breach fallout.
If you operate in finance, healthcare, or SaaS, compliance-driven requirements will shape your policy structure.
Scaling coverage this way provides protection proportionate to your business model. It also helps avoid overspending on unnecessary add-ons that insurers often bundle in. The goal isn’t to buy the biggest policy; it’s to buy the one most relevant for your business.
First-Party vs Third-Party Cyber Insurance Coverage Policy
Think of cyber insurance as a two-sided defense system. One side protects your business, the other protects everyone your business touches.
- First-party coverage protects you. It covers internal losses like:
- Ransomware attacks on your servers
- Lost or corrupted files
- Business interruption and recovery costs
- Third-party coverage protects others. It kicks in when your breach causes harm to:
- Customers whose data is exposed
- Vendors or partners affected by your systems
- Clients who sue for damages or regulatory violations
Most policies include both, but many lean heavily toward first-party benefits. A well-rounded cyber insurance coverage checklist ensures both sides are covered, because even if your systems survive, someone else’s loss could still become your liability.
Common exclusions to watch for:
- Poor patching or outdated software
- Inadequate or missing backups
- Ignored known vulnerabilities
Be aware that if your IT documentation shows negligence, your claim could be denied, regardless of your premium.
Policy Traps to Watch When Creating Your Cyber Insurance Coverage Checklist
The fine print in cyber insurance policies often hides costly surprises. Before signing or renewing, watch for these common traps:
- Retention Clauses: These work like deductibles. You pay a set amount before coverage kicks in. Misreading them can leave you thousands out of pocket.
- Vendor Liability Gaps: Some policies exclude breaches caused by third-party providers. If your cloud vendor or payment processor is compromised, you could be left holding the bill.
- Insufficient Coverage Limits: A low-cost policy might not stretch far enough. Make sure your limits reflect real-world costs for downtime, data recovery, and legal defense.
- Static Policies: Your business evolves, so your policy should too. If you expand into new markets, adopt new software, or face new regulations, update your terms before renewal.
- Poorly worded underwriting requirements; overestimating your security posture. You will want to err on the side of caution when filling out environment questionnaires for the underwriter. Don’t say you have X when you are not sure or only partially support it. It is better to say you don’t have it and to pay a little more premium than to overreport your capacity and have a claim denied later.
Each of these missteps can violate core cyber insurance policy requirements, giving insurers grounds to deny claims. Always read line by line and don’t hesitate to bring in legal or cybersecurity experts to translate the jargon into plain English.
The Pre-Policy Prep That Lowers Your Premium
Strong cybersecurity habits don’t just protect your business; they also earn trust from insurers. Before applying or renewing your cyber insurance policy, tighten these key areas to reduce risk and lower premiums:
- Regular Security Audits and Vulnerability Testing: Show that you’re proactive. Routine assessments help identify and fix weak spots before attackers exploit them.
- Multi-Factor Authentication (MFA): Required by most insurers. MFA protects remote users and admin accounts from credential theft.
- Incident Response and Business Continuity Plans: Insurers reward readiness. A documented response workflow signals that your team can act quickly and minimize damage.
- Employee Cybersecurity Training: Human error is still the top entry point for attacks. Track your training programs and phishing simulations to prove awareness and discipline.
Following these steps meets cyber insurance policy requirements, strengthens your defenses, and keeps your records airtight.
When and How to Update Your Cyber Insurance Coverage Checklist
Cybersecurity is constantly evolving. A policy that fit last year may now leave critical gaps. You’ve likely outgrown your coverage if:
- You’ve added new vendors, cloud apps, or data sources
- Your digital footprint has expanded beyond your policy’s scope
- You now operate under compliance frameworks like HIPAA, GDPR, or PCI DSS
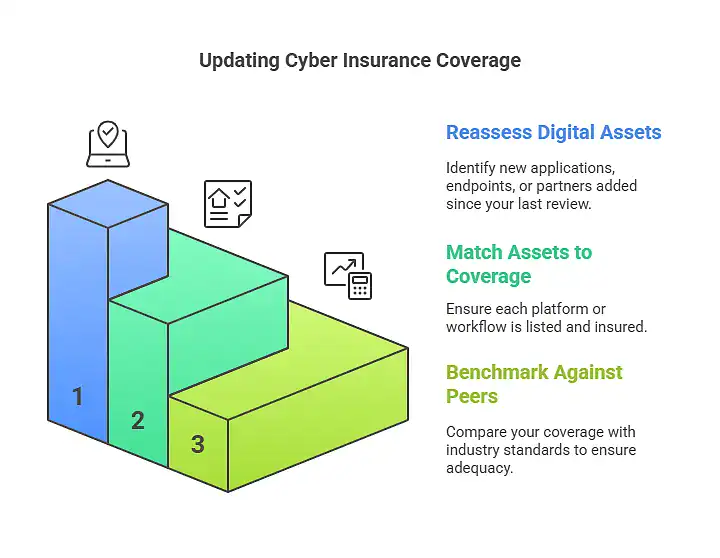
Keep your checklist current with this simple 3-step annual review:
- Reassess Your Digital Assets: Identify new applications, endpoints, or partners added since your last review.
- Match Each Asset to a Coverage Item: If a platform or workflow isn’t listed, it likely isn’t insured.
- Benchmark Against Industry Peers: Compare your policy features and costs with others in your sector to spot gaps or overspending.
A yearly update ensures your cyber insurance coverage checklist stays relevant, realistic, and ready for whatever threat comes next.
Cyber Insurance Coverage Gaps Businesses Commonly Overlook
Even the best policies can have blind spots. Before you close the deal, compare your policy against these frequently missed coverage areas. Addressing them can mean the difference between a setback and survival.
| Coverage Gap | What It Means | Business Impact |
| Social Engineering Fraud | Attacks that trick employees into transferring funds | Financial loss without system compromise coverage |
| Reputation Damage | Costs tied to brand recovery and lost trust | Long-term customer churn and sales decline |
| Intellectual Property Theft | Loss or theft of proprietary data or code | Competitive disadvantage, legal disputes |
| Hardware Replacement | Damage to physical servers or devices from digital incidents | Extended downtime, costly replacements |
| Regulatory Updates | Policies not aligned with new data protection laws | Fines, compliance gaps, revoked certifications |
These gaps often surface after an incident, when it’s too late to adjust. Add them to your cyber insurance coverage checklist during renewal to stay fully covered.
Partner With a Trusted IT Support Provider in Austin to Prevent Breaches and Lower Cyber Insurance Premiums
A strong cyber insurance coverage checklist identifies gaps, aligns coverage with your actual risk, and ensures your business can respond quickly to cyber threats. Businesses that neglect this often face steep costs, downtime, and reputational damage.
Gravity Systems is a trusted MSP that strengthens your IT defenses and lowers premiums by implementing robust security controls, from multi-factor authentication to proactive monitoring.
With 24/7/365 helpdesk services since 1997 and a 90-second average response time, Gravity Systems delivers rapid, reliable support when it matters most.
Contact our Austin IT support team to strengthen your entire security posture and protect your business with smarter, safer IT.



